Hi,
Everything in this post is wrong.
As with many CVE’s, this one is sensationalist FUD.
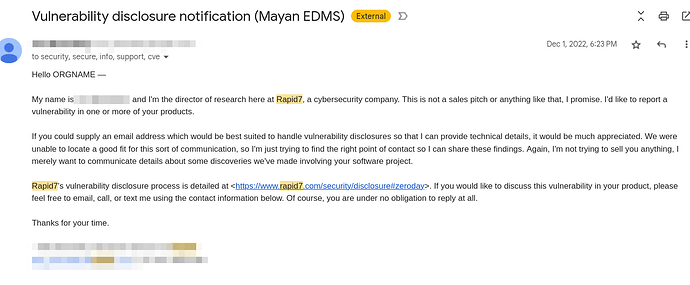
Notification
Unfortunately, none of these vendors were able to respond to Rapid7’s disclosure outreach,
Their communication was a generic template not much different from all the cybersecurity scams, phishing attempts or bounty requests we receive daily.
Our security communication policy is clear and available online.
https://docs.mayan-edms.com/chapters/security.html#security-faq
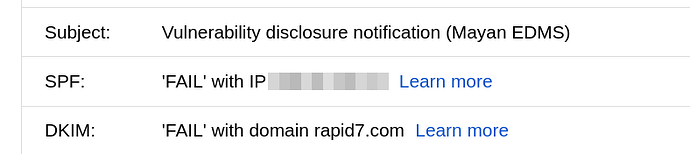
Even in retrospect it is still hard to identify this email as legitimate or trustworthy.
Unpatched
We closed the issue regarding CVE-2022-47419 immediately.
https://docs.mayan-edms.com/chapters/security.html#cve-2022-47419
https://docs.mayan-edms.com/releases/4.3.6.html#tags
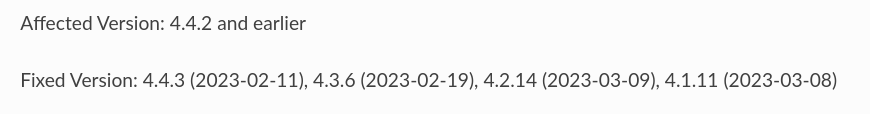
Backports
It is likely the vulnerability exists in previous versions of the software.
It was backported immediately to the two supported versions (4.4 and 4.3) and a few weeks later to even end-of-life versions (4.2 and 4.1).
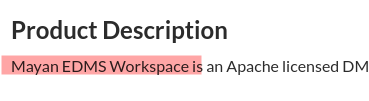
Confused project
Also the CVE was researched by someone that is not familiar with Mayan EDMS.
In the absence of an update from the vendor, administrators should limit the creation of anonymous, untrusted users for the affected DMS, since all users have access to the tagging system by default.
Mayan EDMS does not support creating anonymous untrusted users.
Besides a valid account, access to the tagging system also requires either the tag create or tag edit permissions. Therefore this assertion is completely wrong.
Severity
A typical attack pattern would be to steal the session cookie a locally-logged in administrator is authenticated with, and reuse that session cookie to impersonate that user to create a new privileged account.
The researcher is not familiar with Django.
Since version 1.4 (March 23, 2012) Django has included the httponly attribute for the session cookie. This means that the session cookie data, including sessionid, is no longer accessible from JavaScript. Django 1.4 release notes | Django documentation | Django
It is not possible to steal or hijack the session via JavaScript on its own or via XSS because the session cookie is not available to JavaScript.
Exploit potential
A slightly more subtle and extensible attack would be to hook the victim’s browser session and inject the attacker’s own commands under the identity of the hooked user, using BeEF or similar post-exploitation tooling.
Once enabled, the attacker would then have access to all stored documents, which may be critically important to the targeted organization.
Since the session cookie cannot be hijacked via JavaScript this is all implausible and just sensationalistic speculation.
Any usage of this weakness remains logged in the event system making it easy to track down any bad actors.
Due to all these factors, the surface of attack of this weakness is very limited, if any.
Exploits
An XSS vulnerability was discovered in the Mayan EDMS DMS. Successful XSS exploitation was observed in the in-product tagging system.
CVE-2022-47419 Exploitation
CVE-2022-47419 is a stored XSS in the in-product tagging system. Reproduction steps are below.
Being able to display a text message via a JavaScript alert is not a session hijack exploit.
There are no known actual or theoretical attacks exploiting this weakness to expose or destroy data in Mayan EDMS.
Conclusion
Given the high severity of a stored XSS vulnerability in a document management system, especially one that is often part of automated workflows
XSS are not always a serious security issues specially when they require privileged access from a trusted individual, and used in frameworks where JavaScript does not have access to critical session content.
It is worth nothing the absence of commercial DMS products from the list.
This CVE has been heavily indexed in its wrong and incomplete manner that our own report and summary of resolution does not show up in searches even when adding the “mayan” keyword.
The purpose and outcome of this CVE are clear.